Android Security Analysis Tools, Part Four - MobSF
Contents
This article is part of a series:
Android Security Analysis Tools, part one - JAADAS
Android Security Analysis Tools, part two - DIVA app and AndroBugs
Android Security Analysis Tools, part three - Drozer and QARK
Android Security Analysis Tools, part four - MobSF
We present last part of the series of blog posts dedicated to security analysis tools for Android apps. The tools discussed in the series were suggested by the OWASP Mobile Testing Guide (MSTG). In the previous parts we discussed JAADAS, Androbugs, Drozer and QARK. This chapter will focus on MobSF, which is also suggested by MSTG. The main goal of the overview is to find the best tool that will be also easiest to integrate with existing CI/CD stacks.
Cons
MobSF, also called Mobile Security Framework, is another tool suggested by OWASP MSTG for static analysis of security in mobile applications. It is designed to perform static and dynamic analysis and tests of security on the most common mobile platforms: Android, iOS, and Windows. Unlike the previously discussed tools, MobSF has a graphic UI in the form of a web service. The web service consists of a dashboard that presents the results of the analysis, its own documentation site, an integrated emulator/symulator, and an API that allows users to trigger the analysis automatically. As I mentioned, MobSF supports different mobile platforms, so the user is able to send APK, IPA or APPX files to the dashboard to trigger the analysis process. The process will start when the user sends the application. The tool will decompile it and the analysis will be performed on decompiled source code. The analysis can also be performed on zipped source code.
MobSF is a framework written mostly in Python, with support for JavaScript, Smali code, and shell commands. The most recent version is 1.0Beta, published under the GPL 3.0 license.
The framework is a very powerful tool, especially with its ability to test multiple mobile platforms. This feature is another aspect that distinguishes this tool from the ones previously overviewed. However, the biggest advantage of this framework is certainly the list of the types of analysis and vulnerabilities that it can find. Here are some of the most interesting features:
- Basic application information scan;
- Application component detection and configuration detection (Activities, Services, Content Providers, etc. for Android);
- Manifest file analysis;
- Source code decompilation;
- Certificate and signing analysis;
- Permission analysis and classification;
- Native library analysis (e,g, detection of misconfigured ASLR for C libs);
- SDK misuse detection;
- Code issues (e.g. logs with sensitive information, tmp files that are not deleted, execution of raw SQL queries, etc.);
- Malware detection;
- External API communication detection;
- Resource analysis;
- Detection of sensitive information in the code or resources;
- etc.
Additionally, it is possible to perform dynamic analysis after finishing the static one. It is possible thanks to the emulator integrated in the device. The emulator allows you to create different environments, test the app, and check logs published during analysis.
Integration
MobSF publishes its source code in this repository on GitHub. Additionally, the framework is published in ready-to-use form as a Docker container. This container is published in a Docker repository called DockerHub. Thanks to this approach, installation of the MobSF service is very easy. To install and run the tool you only need to have Docker installed and then you can run these two commands:
docker pull opensecurity/mobile-security-framework-mobsf
docker run -it -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
The first command will download the container DockerHub. The second will run Docker with the container on port 8000. Thanks to this, you can easily incorporate the tool in your tool stack. Additionally, integration is even more easy thanks to the API that is an integrated part of the MobSF framework. Thanks to this integrated API you can easily send applications, trigger analysis, and collect results using standard HTTP requests. This makes integration very easy and flexible. Unfortunately, the framework does not contain any kind of access management, so the dashboard is easily accessible. Additionally, the tool does not support HTTPs encryption. This means that to secure the result of the analysis the tool should be setup in a local network, inside the CI environment, or in any place that is separated from Internet access. Of course, the source code of the tool is available, so it is possible to implement additional access management features. However, we need to remember that there is no such features in the official release.
Interface
As it was mentioned, GUI is one of the things that distinguishes the tool. It increases the usability of the tool because it is much easier to manage it via a web browser than just using the console. This makes the tool more user friendly, so the time needed to perform analysis and review the results can be significantly decreased.
As you can see, the interface is a simple Python-based web page. All of the analysis is performed under the hood on app upload stage. Then the framework will generate a results web page that you can see in the above screenshot. It contains all the information about the analysed application split into categories. The categories are based on the areas in which the app was analysed. As you can see, the main menu also contains the Download Report and Start Dynamic Analysis buttons. The first one will generate a report in the form of a PDF file. It will contain all of the results that are displayed on the web page. Start Dynamic Analysis will launch a web page that contains an emulator.
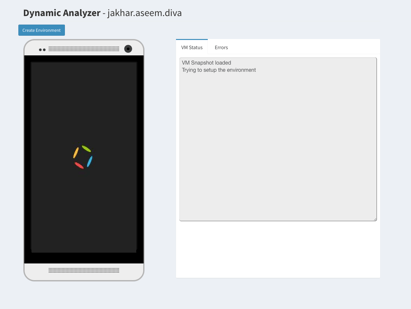
Unfortunately, the emulator still has some issues and is hard to run. I hope that this feature will soon be fixed - the future looks very promising.
It is also worth mentioning that the main dashboard contains links to the API documentation and to the history web page. The history page contains a list of the recent scans and their results. Recent scans can be easily explored thanks to the included search engine.
Pros
- Easy to install - based on a Docker container;
- Easy to integrate with existing CI/CD stack using the integrated API;
- Extensive graphic interface;
- Complex and multilayer analysis with app decompilation;
- Ready to analyse security on multiple mobile platforms - Android, iOS, and even Windows;
- Can perform manual tests directly on analysed app using built-in emulator/symulator.
- Can compare analysis results thanks to the historical results stored by the framework;
- Can generate and download reports in PDF;
- Can emulate system events, manage system processes or analyse files on the device using the integrated emulator;
- Is constantly developed;
- Open-source
- Based on well-tested tools like apktool and Dex2jar;
- Can generate results in JSON.
Cons
- Missing access management features;
- The framework is still in beta;
- It is hard to run Android the emulator.
Overview
Certainly, MobSF is a very powerful and complex tool. Additionally, as the only one of the tools discussed, MobSF has an extensive graphical interface, which makes it more user friendly. Thanks to these aspects the tool is a perfect fit for fast analysis of mobile apps or regression tests. Moreover, thanks to the easy installation and integrated Web API, the tool can also be incorporated into your current CI/CD stack. In my opinion, it is a great tool that will perfectly fit into many existing processes thanks to its flexibility. I hope that the tool will continue to be developed and improved.
What's next?
After conducting our reviews of several tools suggested by OWASP, we decided to choose two tools: QARK and MobSF. In our opinion they are the best in terms of functionality. Both of them are also compliant with our secondary goal - they are easy to integrate with existing stacks. Due these aspects, we will conduct a test implementation of both tools in our team. The tests will allow us to collect more information about which of them is more suitable for our needs. After tests, we will select one tool and publish a short case study about our conclusions.
Continue reading:
Android Security Analysis Tools, part one - JAADAS
Android Security Analysis Tools, part two - DIVA app and AndroBugs
Android Security Analysis Tools, part three - Drozer and QARK
Photo by Quentin Kemmel on Unsplash
