How to Develop a Cybersecurity Strategy? Step-by-Step Guide

Contents
Digital acceleration has contributed to the expansion of IT systems used by organizations. These complex systems are not only a tool but in many cases, the main business drivers.
That means that they operate on a key business value – the data. This data is of great worth to organizations, the loss of which could have serious negative consequences.
The security of this information should be a priority, not only for cybersecurity teams but the whole organization. To effectively protect the data, you need to define a cybersecurity strategy to help build and develop a security management plan to protect your systems.
Read this short guide on how to build an effective cybersecurity strategy.
Define your context
For cybersecurity strategy to be as effective as possible, it should be tailor-made. That means you should consider both internal and external factors that may affect the shape of your business security architecture or a specific IT system.
What should you take into account when setting the context?
First of all, your business. Answer the questions:
- What types of data are processed by your business processes?
- Which of these data types are the most valuable and why?
This knowledge will allow you to find other factors that may affect the shape of your cybersecurity strategy.
Regulations
External regulations will have an additional impact on the shape of your strategy. They will impose requirements on the business and IT systems, which you must take into account in the planning phase. Omitting regulatory requirements may have business consequences, for example, financial penalties. Therefore, it is critical to identify what regulations you should consider when designing a cybersecurity strategy.
Company culture
When planning a cybersecurity strategy, analyze the current culture of your tea or organization. Probably, the organization has some valuable cultural elements that make it unique. Building security against an organizational culture will be challenging and most likely will make the strategy and security elements ineffective.
On the other hand, the current culture can also have disadvantages and promote bad habits that are worth addressing in the strategy.
Know your assets
To plan a security strategy well, name what you want to protect:
- What types of data do you process?
- How is this data used?
- In what processes is this data used?
- In addition, identify the tools that process this data.
A defined resource register will allow you to improve recognizing security threats and determine the risk of individual elements. This is one of the first steps necessary to outline your strategy.
Define your threat landscape
Have a list of resources, and identify the threats associated with them. Each of them is a separate attack vector. A different attack vector means distinct means of protection and prevention. Identifying these threats is a key element in designing security architecture in line with defense-in-depth principles.
Identify risks
Each threat can have an impact on your business. Some have a bigger impact and some have a smaller impact. You do not have to worry about every threat right away.
However, some require immediate attention. How do you identify which are critical and which are less important? Risk analysis is the answer.
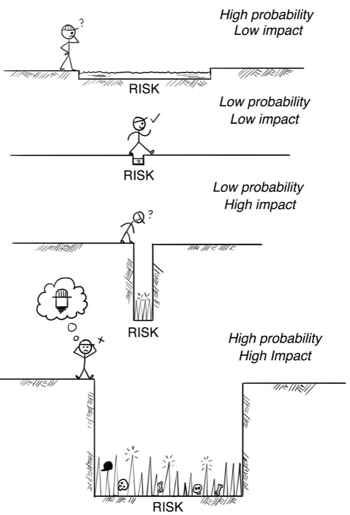 Source: Twitter
Source: Twitter
In this process, you determine the probability of occurrence for each threat and what the impact will be on your key resources if the threat occurs.
Thanks to this, you will be able to determine the possible costs of the occurrence of risks and determine what the "risk appetite" is (the level of risk acceptable for you). Risk analysis helps you easily set up the priorities of cybersecurity architecture elements.
Prevent
Once you know the context for the security architecture, you need to plan risk prevention mechanisms. Prevention and any proactive action, along with reactivity, are at the core of cybersecurity architecture.
Select security controls and design security architecture
To build the security architecture for your business, you need to choose the proper security controls. This selection should reflect the identified threats.
It will help you to build a security architecture based on defense-in-depth. That means security architecture tailored to your business, based on multi-layered resource protection that responds to various cyber threats.
Prioritize
Implementation of safety components is complex, time-consuming, and costly. Thus, you cannot implement everything on the spot.
In addition, some security measures, especially those poorly selected, may have damaging side effects for the business and - for example, they might slow it down. To avoid it, prioritize the implementation of security controls.
How do define priorities for the implementation of cybersecurity controls? Base them on a predetermined risk.
Implementation of security measures should be about risk mitigation. Risks should be mitigated starting from the highest to the lowest. Thanks to this rule, you can determine priorities for implementation. Remember to balance these priorities against the budget.
Implement
The prioritized control implementation plan is ready. So now it is time to implement.
Remember that the implementation of security controls will affect your business operations. To minimize the impact and possible interruptions, you need to cooperate with teams that will be affected by the implementation.
For the elements of the strategy to work effectively, teams must have an appropriate threat-awareness level. They also need to know how the security controls should work.
This requires cooperation and joint development of the most effective solutions. Enforcing solutions "from the top" without cooperation will make implementation difficult, and users will not use tools and processes in the way they were intended.
Test
The implementation of security elements is just the beginning of your path. The next step of the strategy should be tests of the security system.
Tests verify the level of safety and effectiveness of your security measures. Notably, the strategy should assume periodic and regular tests and audits of security. A single test is not enough to address the ever-changing IT ecosystem.
In addition to verifying the security level, the tests will provide you with information about the weaknesses of your system. It will allow you to improve the security architecture based on the identified vulnerabilities. Tests are, therefore, a critical element that provides the basis for continuous improvement of the system.
React
Proactive controls for cyber threats are just half of the way. To effectively protect your business and IT systems, you have to react to events. To respond effectively to events like security incidents, you need to add a few more elements to the strategy.
Define KPIs and KRIs
To monitor the applications, system, environment, or the entire IT of your organization, you need to define what you want to track in such a system.
For monitoring to be effective, you should define a set of parameters. Their state will reflect the state of the entire system.
Key Performance Indicators (KPIs) are a fairly obvious choice for monitoring the health of your business. However, if you define KPIs as availability, confidentiality, or integrity, they can be used as security metrics. Monitoring KPIs can show you that something unwanted is happening in the system.
You can use Key Risk Indicators (KRIs) similarly. You can define the parameters that determine the risk. For example, thresholds for failed login attempts, or thresholds for the number of requests to the system for critical endpoints.
Specifying KRIs allows you to detect threats even before they compromise the system. In determining KRIs, the pre-performed risk modeling and risk analysis will certainly help.
Well-defined parameters allow you to detect anomalies in the system and react quickly enough to prevent harmful events or minimize their effects when you are unable to prevent them.
Monitor
It is essential to define KPIs and KRIs and track them.
However, you can do more in terms of monitoring. You can collect metadata from the behavior of users of your systems and their interactions with your resources. Thanks to appropriate aggregation and analysis of such data and metadata, you can detect anomalies in the system and more efficiently react to potential incidents.
The key here is to choose the right tools for what you want to monitor. To assist you in determining the boundary conditions for monitoring tools, you can use the results of risk assessments.
Respond to incidents
Detecting incidents is the basis for counteracting. But what to do when you notice an incident? Neutralize, control damages, and conclude.
Another crucial part of your cybersecurity strategy is a defined security incident handling procedure. It should include incident classification instructions, contamination and eradication procedures, escalation paths, and mitigation scenarios.
Remember also to do a post-mortem analysis of any incidents. The conclusions from the analysis carried out after the incident are, after the security tests reports, another valuable element that will allow you to improve security in the future.
Repeat – continuous improvements
Security is a process. It is a well-known slogan – but what does it mean exactly? The elements of security, especially cybersecurity, should not only be implemented but should be maintained and constantly developed.
Deming Cycle
A well-implemented cybersecurity strategy should define a cycle of constant adjustments and improvements. One of the exemplary models describing such a cycle is the Deming Cycle (PDCA cycle). It describes the principle of continuous improvement and is the basis for building IT systems based on best practices and standards (e.g., ISO 27001).
 Source: Wikipedia
Source: Wikipedia
Check and act
The essential element of the continuous development of security is the verification of the current level. You can do it through tests and security audits. The output from such tests or audits is a report on the weaknesses of your system, and it is a starting point for the next improvement.
Test and audit results are just one source of data required to start the next phase of the improvement cycle. Another source should be summaries and conclusions from incidents that have happened, and findings from observing defined KPIs and KRIs for your systems.
Plan and do
To fully understand and develop security on an ongoing basis, the strategy must follow a full cycle of improvement. The current state of your security (tests results and output of incident analysis) should be the entry point for another round of resource checks, risk analysis, and threat modeling.
Why should you do it again? – To compare the state of your security with new threats, attack vectors, vulnerabilities, and outdated technologies. This way, you will find more threats and risks to address, which will then have to be tested again. And the continuous improvement loop is then closed.
Build on best practices and battle-proven standards
Use best practices and proven standards when defining your cybersecurity strategy.
For this purpose, you can use very general frameworks and criteria. They can be more specific, once tailored to a particular organization model, IT system architecture, or even individual technologies. Of course, the more specific, the more detailed instructions and checklists you get.
Relying on standards has another advantage. It makes it easier to adapt to legal regulations that may apply to the business.
For example, if your organization and IT systems comply with the ISO 27001 standard, it will be much easier and cheaper to implement GDPR requirements. If your tool meets the requirements of the OWASP ASVS, it will be much easier to be compliant with HIPAA or PCI-DSS.
This is because the standards are based on the same key methods of securing business processes.
Moreover, building based on best practices allows you to avoid common problems encountered in the implementation of systems and security strategies.
A good example here would be the DevSecOps model for software development. It emphasizes integrating top-to-bottom security. Since cybersecurity experts are part of project teams, security implementation does not slow down publishing cycles, and the security elements themselves are an integral part of the software produced, called “secure-by-design.”
Build awareness
Statistics show that human error is the number one cause of security problems. This is mainly due to the low awareness of threats related to cybersecurity. This applies to both system users and technical people working on creating, configuring, and managing IT systems.
Therefore, building awareness is one of the crucial elements of a cybersecurity strategy.
Hence, a defined awareness-building program should be an obligatory element of it. You should determine how to periodically test and gain awareness of all stakeholders in the system and business. Regardless of whether we are talking about users, the technical team, or the back office of the organization. Each of these areas should be covered in the cybersecurity awareness program.
In addition, you need to think carefully about how to train in cybersecurity. Testing, training and reading policies alone are not enough.
Package all these elements into a simple, transparent, and interesting form. The form of building awareness has an enormous impact on its human reception.
Building awareness based on positive emotions and appropriate narratives is the key to better understanding. Modern approaches to building awareness are based on building communities and integrating security elements into everyday work and team culture.
A good example is the DevSecOps approach, where safety experts become an integral part of project teams. Demolishing silos and glass ceilings significantly increase awareness.
This allows teams to learn best practices by developing them themselves. As practice shows, this approach brings the best results when it comes to awakening awareness.
